The digital world has revolutionized communication and information sharing, but this interconnectedness also presents vulnerabilities. One such threat is the monkey in the middle origin, a cybersecurity attack where malicious actors intercept communications between two parties. This hidden interception allows attackers to steal sensitive data like passwords, financial information, and personal details, compromising user privacy and security. Understanding how these attacks work, their various forms, and the risks they pose is crucial for implementing effective protection measures.
This article delves into the intricacies of monkey in the middle origin attacks, exploring their mechanisms, different types, potential consequences, and essential cybersecurity practices to mitigate these threats. By gaining a comprehensive understanding of this attack vector, individuals and organizations can strengthen their defenses and safeguard their digital assets.
Man in the Middle Attack Explained
A monkey in the middle origin attack occurs when an attacker positions themselves between two communicating parties, acting as a relay for their data exchange. This interception allows the attacker to eavesdrop on the conversation, modify messages, or even impersonate one of the legitimate users. The attacker can achieve this by exploiting vulnerabilities in network infrastructure, using malicious software, or manipulating communication protocols.
Imagine Alice sending a confidential email to Bob. In a typical scenario, their communication travels directly between their devices. However, in a monkey in the middle origin attack, an attacker named Eve intercepts this communication. Eve can then read the email content, alter it before forwarding it to Bob, or even impersonate Alice and send a fraudulent message to Bob.
The success of these attacks relies on the attacker’s ability to establish trust with both parties. They might achieve this by posing as a trusted server or using social engineering tactics to trick users into connecting to their malicious network. Once the connection is established, the attacker can gain access to sensitive information flowing between the two parties.
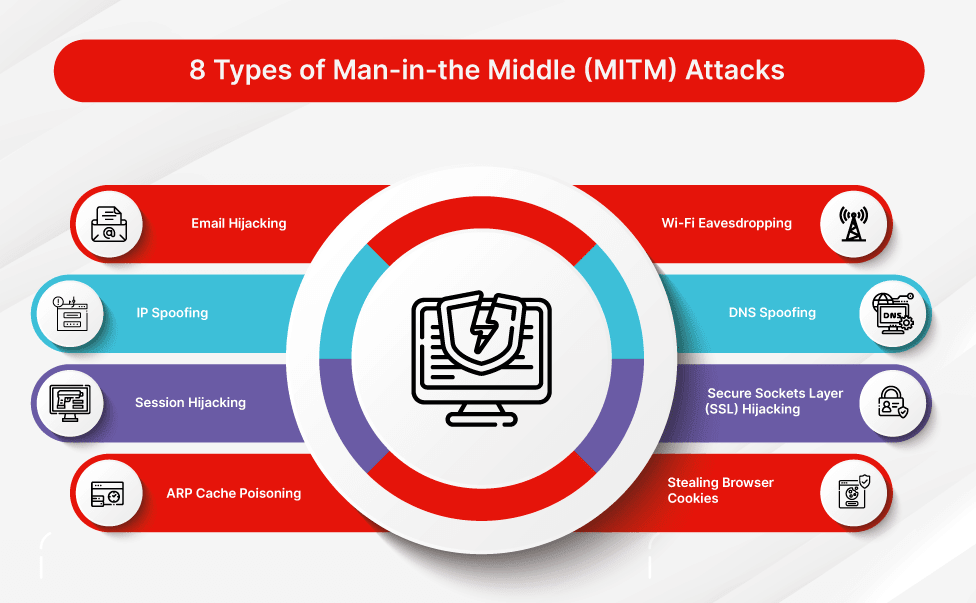
Types of MITM Attacks
Monkey in the Middle origin attacks can manifest in various forms, each exploiting different vulnerabilities and employing distinct techniques. Some common types include:
DNS Spoofing
DNS spoofing involves manipulating the Domain Name System (DNS) to redirect users to malicious websites instead of legitimate ones. When a user enters a website address, their device queries the DNS server for the corresponding IP address. An attacker can intercept this query and return a fake IP address, leading the user to a fraudulent site designed to steal credentials or install malware.
ARP Spoofing
ARP (Address Resolution Protocol) spoofing targets local networks by associating a malicious MAC address with a legitimate IP address. When devices on a network need to communicate, they use ARP to resolve IP addresses to corresponding MAC addresses. An attacker can exploit this process by sending fake ARP messages, tricking devices into associating their own MAC address with the target’s IP address. This allows the attacker to intercept and manipulate all communication flowing between those devices.
SSL/TLS Hijacking
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a protocol used to encrypt online communications, ensuring secure data transmission. However, attackers can exploit vulnerabilities in SSL/TLS implementations to hijack connections and eavesdrop on sensitive information. They might use techniques like man-in-the-middle attacks to intercept the handshake process, inject malicious code, or decrypt encrypted data.
Risks of Man in the Middle Attacks
Monkey in the middle origin attacks pose significant risks to individuals and organizations alike. The consequences can range from minor inconveniences to severe financial losses and reputational damage. Some key risks include:
Data Breaches
The most immediate risk is the theft of sensitive data. Attackers can steal passwords, credit card information, personal identification details, and other confidential information during a monkey in the middle origin attack. This stolen data can be used for identity theft, financial fraud, or blackmail.
Malware Infections
Attackers often use monkey in the middle origin attacks to deliver malware to unsuspecting users. By intercepting legitimate website traffic, they can inject malicious code into web pages or redirect users to websites hosting malware downloads. Once installed, malware can steal data, spy on user activity, or take control of infected devices.
Reputational Damage
If an organization falls victim to a monkey in the middle origin attack and sensitive customer data is compromised, it can suffer severe reputational damage. Customers may lose trust in the organization, leading to decreased business and potential legal repercussions.
Protecting Against MITM Attacks
Implementing robust security measures is crucial for mitigating the risks associated with monkey in the middle origin attacks. Here are some essential steps individuals and organizations can take:
Use Strong Passwords and Multi-Factor Authentication
Strong passwords and multi-factor authentication (MFA) add an extra layer of security to online accounts, making it more difficult for attackers to gain unauthorized access. MFA requires users to provide multiple forms of identification, such as a password and a one-time code sent to their phone, before granting access.
Keep Software Updated
Regularly updating software patches vulnerabilities that attackers can exploit. Software updates often include security fixes that address known weaknesses, reducing the risk of successful monkey in the middle origin attacks.
Install Antivirus and Firewall Software
Antivirus and firewall software act as barriers against malware and unauthorized network access. Antivirus programs detect and remove malicious software, while firewalls control incoming and outgoing network traffic, blocking suspicious connections.
Be Cautious of Public Wi-Fi Networks
Public Wi-Fi networks are often unsecured and vulnerable to monkey in the middle origin attacks. Avoid accessing sensitive information on public Wi-Fi unless you are using a VPN (Virtual Private Network) to encrypt your connection.
Cybersecurity Best Practices
Beyond specific security measures, adopting good cybersecurity practices is essential for minimizing the risk of monkey in the middle origin attacks and other cyber threats:
Educate Yourself and Others
Staying informed about cybersecurity threats and best practices is crucial. Regularly update your knowledge about common attack vectors, phishing scams, and social engineering tactics. Share this information with colleagues, family members, and friends to promote a culture of cybersecurity awareness.
Be Skeptical of Unsolicited Emails and Links
Be cautious when opening emails or clicking on links from unknown senders. Phishing attacks often use monkey in the middle origin techniques to trick users into revealing sensitive information. Verify the sender’s identity before clicking any links or providing personal details.
Use Secure Browsing Practices
Always ensure you are browsing websites using HTTPS (Hypertext Transfer Protocol Secure). The “S” indicates that the website uses encryption to protect your data during transmission. Look for the padlock icon in the address bar and verify the website’s SSL certificate.
Conclusion
Monkey in the middle origin attacks pose a significant threat to individuals and organizations alike, enabling attackers to intercept sensitive information, deliver malware, and cause widespread damage. Understanding the various types of monkey in the middle origin attacks, their potential risks, and implementing robust security measures are crucial for mitigating these threats. By adopting strong passwords, multi-factor authentication, keeping software updated, using antivirus and firewall software, being cautious on public Wi-Fi networks, and practicing good cybersecurity habits, individuals and organizations can significantly reduce their vulnerability to monkey in the middle origin attacks and safeguard their digital assets.